Deepfake Technology – It refers to the use of artificial intelligence (AI) and machine learning algorithms to create highly realistic synthetic media, such as videos, images, or audio recordings, that depict individuals saying or doing things that they never actually said or did.
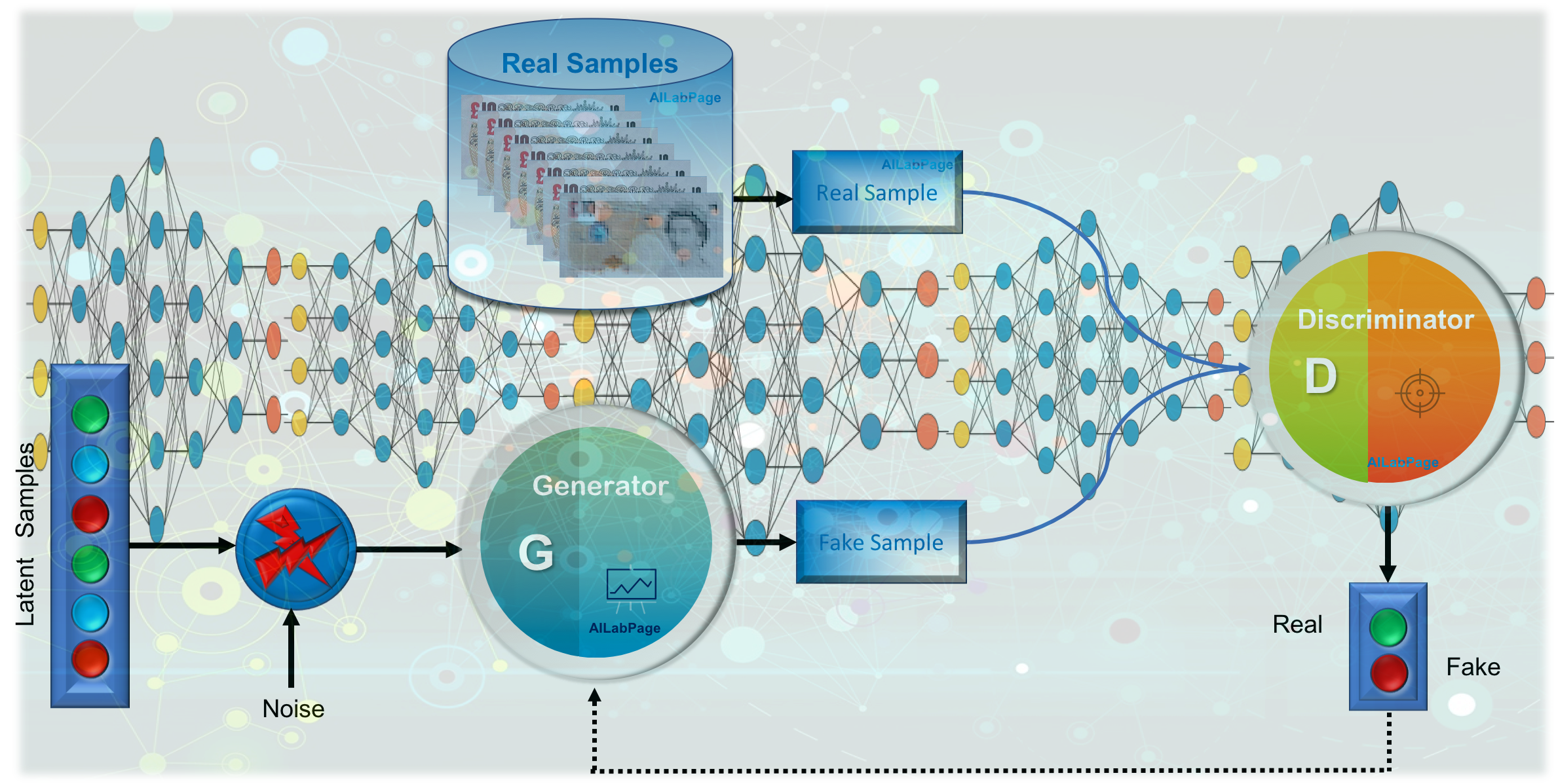
This technology utilizes deep learning techniques, particularly generative adversarial networks (GANs), to superimpose the likeness of one person onto another, enabling the manipulation of facial expressions, gestures, and speech patterns. Deepfakes can be used for various purposes, including entertainment, political satire, and malicious deception, posing significant ethical, legal, and societal challenges.
The Looming Threat: Deepfakes and Counterfeit IDs
Deepfakes are fake videos or pictures made by computers. They look real but are actually made using special computer programs. These fake videos can show people doing or saying things they never did. They are a big problem because they can trick people and spread false information.
Counterfeit IDs are fake identification cards. They look just like real ones, like driver’s licenses or passports, but they are made illegally. People use them to pretend to be someone else or to do things they’re not allowed to do.

Both deepfakes and counterfeit IDs are getting more common and better made. This means it’s harder to tell what’s real and what’s fake. It’s important to be careful and not trust everything you see, especially online.
These fake videos and IDs cause a lot of problems, like spreading lies or helping people do bad things. We need to find ways to stop them, like making better technology to detect them and teaching people how to spot them.
Real-World Examples – Impact
Deepfake technology has permeated various aspects of society, leaving a profound impact on individuals and institutions alike. Through advanced manipulation of audio and video content, deepfakes have emerged as potent tools for deception, with real-world examples showcasing their disruptive potential across diverse domains. Few examples of real-world cases of harm can be caused by deepfakes and fake IDs i.e. fraud, and misinformation etc

- Misinformation and Political Manipulation: Deepfakes have been used to create fake videos of politicians saying or doing things they never did.
- For example, during the 2020 U.S. presidential election, a deepfake video emerged showing candidate Joe Biden apparently making racist remarks. This video spread rapidly on social media, leading to confusion and attempts to discredit the candidate.
- Financial Fraud: Fake IDs are commonly used in financial fraud schemes. Criminals use counterfeit IDs to open bank accounts, apply for loans, or make fraudulent purchases using stolen identities.
- In 2019, a group of individuals used fake IDs to fraudulently obtain millions of dollars in loans from multiple financial institutions.
- Identity Theft: Fake IDs are often used in identity theft schemes, where criminals impersonate others to gain access to sensitive information or commit crimes in their name.
- For instance, criminals may use fake IDs to access secure facilities, bypass security measures, or engage in illegal activities without being detected.
- Reputation Damage: Deepfake videos can damage a person’s reputation or career by portraying them engaging in inappropriate or criminal behavior.
- In 2018, a deepfake video of actress Scarlett Johansson engaging in explicit acts went viral online. Although quickly debunked as fake, the video caused significant embarrassment and distress to the actress.
- National Security Threats: Deepfakes can pose significant national security threats by spreading false information or inciting conflict.
- For instance, in 2019, a deepfake video emerged purporting to show the president of Gabon, Ali Bongo, giving a speech after he had suffered a stroke. The video led to political instability and raised concerns about the potential for foreign interference in the country’s affairs.

The proliferation of deepfake technology has yielded a myriad of real-world examples, highlighting its far-reaching impact on society. From political manipulation and financial fraud to identity theft and reputation damage, these instances underscore the urgent need for vigilance and countermeasures against the malicious use of deepfakes.
Demystifying the Techniques: How are they Created?
Deepfakes: Deepfake technology leverages advanced artificial intelligence and machine learning algorithms to manipulate or generate realistic audio, images, and videos. These algorithms analyze and learn from vast datasets of images and videos, enabling them to mimic facial expressions, gestures, and speech patterns with remarkable accuracy.

- Counterfeiting IDs encompasses a spectrum of techniques, from simple photo-editing alterations to intricate holographic replication, all aimed at replicating official documents for fraudulent purposes.
- Fraudsters digitally modify personal details on IDs, such as names and dates of birth, to fabricate false identities, while also employing advanced printing methods to mimic security features like holograms and watermarks.
- Some counterfeiters resort to theft of authentic ID templates or utilize professional-grade equipment to create convincing replicas, employing a variety of tactics to circumvent authentication measures and present counterfeit IDs as genuine documents.
Deepfake creators often use generative adversarial networks (GANs), a type of neural network architecture, to generate highly convincing synthetic media. By training these models on large amounts of data, they can seamlessly swap faces, alter expressions, and even synthesize entirely new content, blurring the line between reality and fiction.
Beyond Detection – The Challenges of Combatting Deepfakes and Counterfeit IDs
In this digital age, the proliferation of deepfake technology and counterfeit IDs presents significant challenges across various domains, from cybersecurity to personal privacy. The sophistication of these deceptive techniques has rendered detection increasingly difficult, posing serious ethical and legal dilemmas. Moreover, the existing legal and regulatory framework struggles to keep pace with the rapid advancements in technology, necessitating comprehensive adaptation to address emerging threats effectively.

- As the prevalence of deepfakes and forged IDs continues to escalate, the need for robust detection mechanisms becomes more pressing than ever.
- Ethical concerns surrounding privacy and freedom of expression further underscore the urgency for effective countermeasures.
- Meanwhile, the evolving legal and regulatory landscape underscores the imperative for adaptation to safeguard against the malicious use of these deceptive tactics.
The rise of deepfake technology and counterfeit IDs has ushered in a new era of deception, where distinguishing between reality and falsity has become increasingly complex. As such, the difficulty of detection presents a formidable obstacle in combatting these fraudulent practices.
Collaborative Solutions: Fighting Back on Multiple Fronts
As deepfake technology and counterfeit IDs continue to evolve, the need for innovative approaches to detection and prevention becomes increasingly apparent. This section explores the role of technology advancements, user education, and collaborative efforts in addressing these complex challenges.
- Technology advancements, such as biometrics and deep learning, are pivotal in enhancing detection and prevention capabilities against deepfakes and counterfeit IDs.
- User education and awareness initiatives are vital in empowering individuals to critically evaluate media content and recognize potential deception.
- Collaborative efforts across industries foster information sharing and cooperation, enabling a unified response to combatting the threats posed by fraudulent practices.
In combating the proliferation of deepfakes and counterfeit IDs, leveraging technological advancements plays a crucial role in detection and prevention efforts. From sophisticated biometric authentication systems to the application of deep learning algorithms, these technologies provide invaluable tools in the ongoing battle against fraudulent practices. Moreover, prioritizing user education and awareness is essential to empower individuals with the skills needed to discern between authentic and manipulated content. By promoting critical thinking and digital literacy, users are better equipped to identify and mitigate the risks associated with deceptive media.
Additionally, fostering collaborative efforts within the industry is paramount to effectively combatting these threats. By promoting information sharing and cooperation among stakeholders, such as technology companies, law enforcement agencies, and regulatory bodies, a united front can be established to tackle the challenges posed by deepfakes and counterfeit IDs head-on.
The Future of Authentication – A Continuous Battle
As the landscape of authentication undergoes rapid evolution, it is essential to anticipate future advancements in deepfake technology and the corresponding countermeasures. This section explores predictions for the future of authentication and emphasizes the importance of proactive engagement and collective responsibility in addressing emerging threats.
- Predicting future advancements in deepfakes and countermeasures is crucial for staying ahead of evolving threats in the authentication landscape.
- A proactive approach to combatting fraudulent practices requires collective action and a shared commitment to safeguarding against manipulated media.
- Encouraging proactive engagement and fostering a sense of collective responsibility are essential in addressing the challenges posed by the future of authentication.
The future of authentication is poised to be a continuous battle between evolving deepfake technologies and the countermeasures designed to thwart them. Predicting the trajectory of these advancements is essential for staying ahead of the curve in combating fraudulent practices. As deepfake technology continues to evolve, it is crucial to anticipate future developments and prepare robust countermeasures accordingly.
This proactive approach requires collective action and a shared commitment to safeguarding against the threats posed by manipulated media. By encouraging proactive engagement and fostering a sense of collective responsibility, stakeholders can work together to address the challenges of tomorrow’s authentication landscape head-on.
Deepfake Dangers and Defense – Insights
Deepfake technology presents a growing concern in today’s digital age, with its potential for widespread misinformation and fraud. This section explores the impact of deepfakes, offers practical tips for staying safe, and provides resources for further information and advocacy.
Relevant statistics and data
- According to a report by Deeptrace Labs, the number of deepfake videos online doubled in 2020, reaching over 300,000.
- A survey conducted by Pew Research Center found that 48% of Americans are very or somewhat concerned about the potential use of deepfake videos to spread misinformation.
Practical tips for staying safe
- Verifying sources: Always cross-reference information from multiple reliable sources to ensure accuracy.
- Scrutinizing media content: Look for inconsistencies in facial expressions, audio quality, and background details that may indicate manipulation.
- Utilizing tools for detecting deepfakes: Several online tools and software applications are available to help users identify deepfake content, such as Deepware Scanner and Reality Defender.
Links to resources for further information and advocacy
- Deepfake Detection Challenge by DARPA: Provides information on ongoing efforts to develop technologies for detecting and mitigating deepfake content.
- Guide to Spotting Deepfakes by the Center for Cyber Security Studies: Offers comprehensive resources and tips for identifying and addressing deepfake threats.
- Advocacy organizations like the Deepfake Accountability Project provide updates on legislative initiatives and advocacy efforts aimed at combating deepfake technology.
Inviting expert commentary or case studies
- Interview with Dr. Hany Farid, a leading expert in digital forensics and deepfake detection, to provide insights into the challenges and advancements in combating deepfake technology.
- Case study on the impact of deepfake videos on the political landscape, featuring perspectives from politicians, cybersecurity experts, and media analysts.
- Panel discussion with representatives from academia, industry, and government agencies to explore the ethical, legal, and technical implications of deepfake technology.
In the ever-evolving landscape of deepfake technology, understanding the implications and staying vigilant against its proliferation is paramount. With the increasing sophistication of deepfake algorithms, the threat of manipulated media poses significant challenges to individuals and organizations alike. According to recent studies, the use of deepfakes for malicious purposes has seen a sharp rise, with instances ranging from political misinformation to financial fraud. In response, it’s crucial for individuals and organizations to adopt proactive measures to protect themselves against these deceptive tactics.
Multifaceted Approach – Combating Deepfakes & IDs
Addressing the surge in Deepfakes and counterfeit IDs requires a multifaceted approach that combines technological innovations, regulatory measures, and public awareness campaigns. Here’s a comprehensive strategy:
- Enhance Detection Technology: Invest in advanced AI algorithms and machine learning models specifically designed to detect Deepfakes and counterfeit IDs. Collaborate with technology companies and research institutions to develop robust detection tools capable of identifying manipulated content with high accuracy.
- Strengthen Verification Processes: Implement stringent verification protocols across various sectors, including finance, government, and social media platforms. Incorporate biometric authentication methods, such as facial recognition and fingerprint scanning, to verify identities and detect fraudulent activity.
- Enforce Regulatory Measures: Enact legislation and regulations to combat the spread of Deepfakes and counterfeit IDs. Establish penalties for individuals and organizations involved in the creation and dissemination of fraudulent content. Work with international partners to harmonize regulations and enhance global cooperation in addressing the issue.
- Foster Industry Collaboration: Encourage collaboration between technology companies, government agencies, and law enforcement authorities to share information and best practices for combating Deepfakes and counterfeit IDs. Establish public-private partnerships to develop joint initiatives and initiatives to tackle the problem collectively.
- Educate the Public: Launch public awareness campaigns to educate individuals about the dangers of Deepfakes and counterfeit IDs. Provide resources and training programs to help people identify and report suspicious content. Promote media literacy and critical thinking skills to empower individuals to discern between real and fake information.
- Invest in Research and Development: Allocate funding for research and development initiatives aimed at advancing technologies for detecting and preventing Deepfakes and counterfeit IDs. Support interdisciplinary research projects that bring together experts from diverse fields to develop innovative solutions to address the evolving threat landscape.
By adopting a comprehensive strategy that combines technological innovation, regulatory measures, industry collaboration, public education, and research and development, we can effectively mitigate the risks posed by Deepfakes and counterfeit IDs and safeguard the integrity of digital content and identities.
Deepfakes: Three Sides of the Coin
Deepfakes, videos or audio manipulated to make it seem like someone said or did something they didn’t, have sparked major debate. Let’s explore their positive and negative aspects, and where the technology is headed:
Benefits
- Creative Expression: Deepfakes can be used for artistic purposes, creating satire, humor, or even educational content. Imagine historical figures “coming to life” to deliver messages or re-enact events.
- Accessibility: Deepfakes can make content more accessible by translating languages in real-time or altering appearances to better represent audiences. This opens up communication and storytelling possibilities.
- Personalization: In personalized learning or training, deepfakes could create tailored scenarios with virtual instructors or characters, enhancing engagement and effectiveness.
Problems
- Misinformation & Propaganda: Deepfakes can be easily used to spread fake news, fabricate events, or damage reputations. Their believability makes them potent tools for malicious actors.
- Privacy Concerns: Deepfakes raise concerns about the unauthorized use of someone’s image or voice without their consent. This can lead to harassment, identity theft, and other harmful consequences.
- Erosion of Trust: The proliferation of deepfakes can erode trust in media, information sources, and even interpersonal interactions. Doubting what’s real can have a chilling effect on communication and public discourse.
Ongoing Developments
- Detection & Correction: Researchers are developing advanced algorithms to detect and debunk deepfakes, focusing on subtle inconsistencies in facial expressions, audio patterns, and other data points.
- Regulation & Ethical Frameworks: Discussions are underway on how to regulate deepfake technology and establish ethical guidelines for its use. This includes transparency requirements, content moderation, and potential legal frameworks.
- Counterfeit Detection Technologies: Companies are developing tools to embed digital watermarks or other markers into media to make them more tamper-proof and easier to verify authenticity.
The story of deepfakes is still unfolding. While challenges abound, continued research and responsible development can unlock their positive potential while mitigating the risks.
Krishna’s Deepfake Detective Work: Exposing a Phony Interview
Krishna, a seasoned pro photographer with a keen eye for detail, found himself entangled in the world of deepfakes when a client approached him with an unusual request. The client, a well-known politician, claimed to have given a video interview to a major news outlet, but the footage seemed “off” somehow. Krishna was tasked with investigating the authenticity of the video.
The Investigation:
- Visual Cues: Krishna meticulously analyzed the video, zooming in on facial expressions, skin tones, and lighting inconsistencies. He noticed subtle differences in eye movements and micro-expressions that didn’t match the natural flow of speech.
- Technical Scrutiny: Using specialized software, Krishna examined the video’s metadata and digital footprint. He looked for signs of manipulation, such as anomalies in compression artifacts or inconsistencies in frame rates.
- Audio Forensics: He isolated the audio track and employed audio analysis tools to detect potential splicing or voice synthesis markers. The analysis revealed subtle inconsistencies in voice pitch and timbre, raising further doubts.
- Cross-Referencing: Krishna didn’t stop there. He scoured the internet for other videos of the politician, comparing facial features, mannerisms, and speech patterns to identify discrepancies.
The Revelation:
After meticulously piecing together the evidence, Krishna concluded that the video was indeed a deepfake. His findings, based on a combination of visual analysis, technical expertise, and cross-referencing, exposed the fabrication before it could cause any damage to the politician’s reputation or spread misinformation.
The Impact:
Krishna’s work not only protected his client but also highlighted the growing threat of deepfakes and the need for vigilance. His example serves as a practical demonstration of how seemingly subtle visual and audio cues can betray a deepfake, even to the untrained eye. It underscores the importance of critical thinking, technical skills, and cross-referencing information in the fight against disinformation.
Additional Notes:
- This is just one example, and the specific techniques used will vary depending on the sophistication of the deepfake and the available resources.
- It’s important to remember that deepfakes are constantly evolving, making detection increasingly challenging.
- Staying informed about the latest developments in deepfake technology and being aware of potential red flags is crucial for everyone in today’s digital age.
By embracing this multifaceted approach, we can effectively combat the spread of deepfakes and counterfeit IDs, preserving trust, integrity, and authenticity in our digital interactions.

Conclusion – As we confront the growing menace of deepfakes and counterfeit IDs, it is abundantly clear that a comprehensive strategy is essential. This strategy must be multifaceted, integrating technological advancements, regulatory frameworks, public education, and collaborative efforts. By enhancing our detection capabilities through investment in advanced AI algorithms, bolstering verification processes with biometric authentication, and enforcing stringent regulations, we can strengthen our defenses against manipulation and fraud. Moreover, fostering collaboration between industry stakeholders, government agencies, and the public is paramount in this endeavor, enabling us to share knowledge, resources, and best practices. Concurrently, educating the public about the dangers of deepfakes and providing them with tools to discern truth from fiction empowers individuals to navigate the digital landscape safely. Lastly, sustained investment in research and development ensures that we remain agile and adaptive in the face of evolving threats.
Feedback & Further Questions
Besides life lessons, I do write-ups on technology, which is my profession. Do you have any burning questions about big data, AI and ML, blockchain, and FinTech, or any questions about the basics of theoretical physics, which is my passion, or about photography or Fujifilm (SLRs or lenses)? which is my avocation. Please feel free to ask your question either by leaving a comment or by sending me an email. I will do my best to quench your curiosity.
Points to Note:
Understanding the optimal application of each “deep learning algorithm” is crucial in combating the surge of deepfakes. This nuanced decision-making process relies on a blend of experience and a deep comprehension of the specific problem at hand. If you believe you’ve identified the right approach, commend yourself for your insight. However, if your initial attempt falls short, view it as a natural part of the learning process and an opportunity for refinement.
Books Referred & Other material referred
- Open Internet research, news portals and white papers reading
- Lab and hands-on experience of @AILabPage (Self-taught learners group) members.
- Self-Learning through Live Webinars, Conferences, Lectures, and Seminars, and AI Talkshows
============================ About the Author =======================
Read about Author at : About Me
Thank you all, for spending your time reading this post. Please share your opinion / comments / critics / agreements or disagreement. Remark for more details about posts, subjects and relevance please read the disclaimer.
FacebookPage ContactMe Twitter ====================================================================

